AI Agents That Close Your Exposure Window
Backlogs don't protect you. Fixes do. Averlon determines what is truly exploitable in your environment and delivers safe fixes directly into developer workflows.
Backed by




Enterprises Reducing Real Exposure with Averlon












Finding Doesn't Shrink Risk. Fixing Does.
Vulnerabilities keep rising - 28,000 in 2023, 48,000+ in 2025. Finding more isn't sustainable. Attackers move in days. Remediation often takes months.
This Exposure Window, the time between finding and fixing, is the real risk.
Closing it is not about finding more. It is about fixing what actually matters.
5 Days
Median time from disclosure to exploit. Attackers move almost immediately.

80% Unpatched
Vulnerabilities still open 30 days after patch release.

200+ Days
Average time it takes organizations to remediate vulnerabilities.

Meet Averlon
The Agentic Remediation Operations platform that closes your Exposure Window.
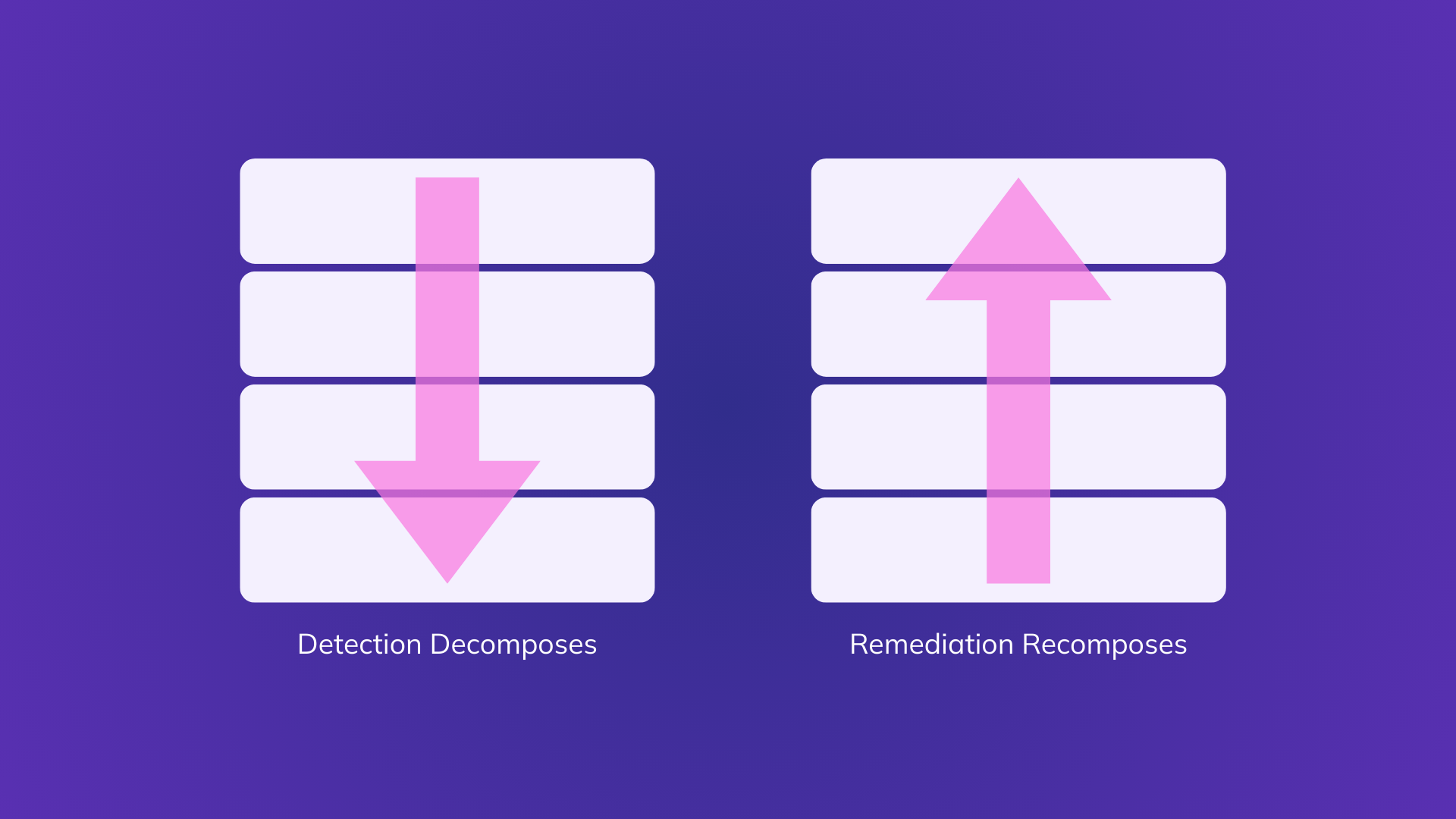
Most tools generate findings and severity scores. They stop at prioritization.
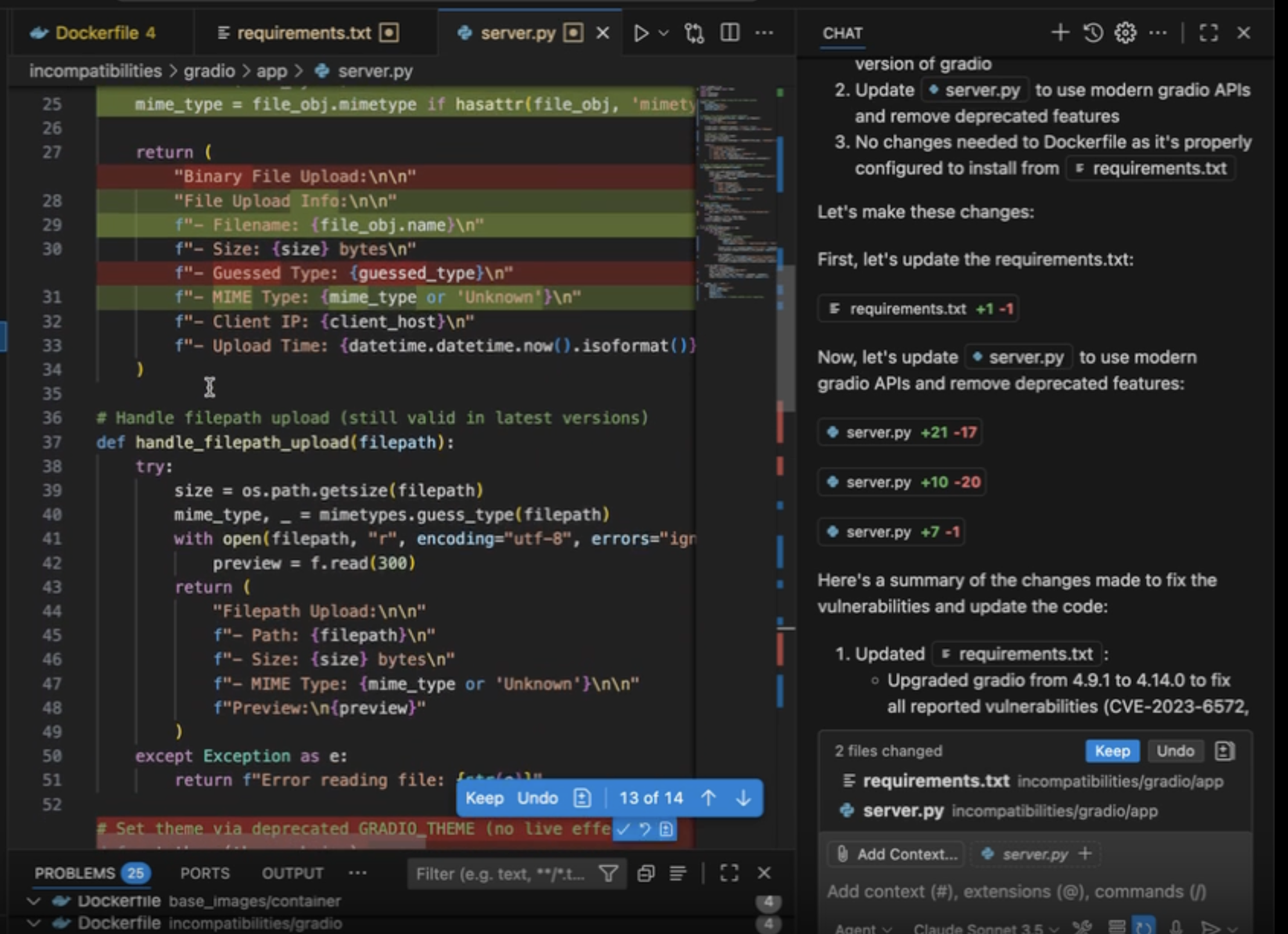
Averlon determines what is materially exploitable in your environment and delivers safe fixes directly into developer workflows.
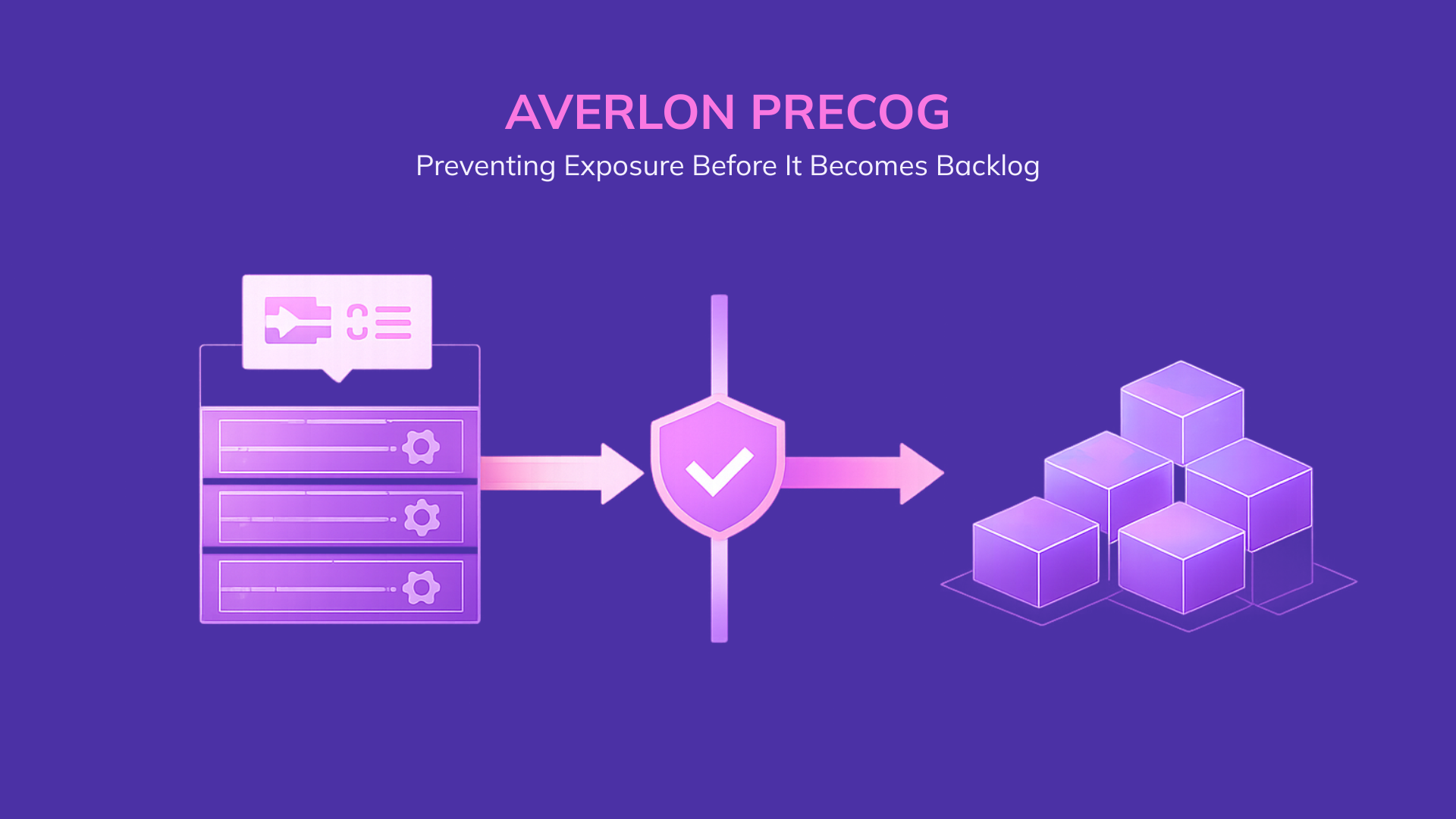
It applies the same reasoning pre-merge, preventing new exposure before it becomes backlog.
Exposures get closed. Backlogs shrink. Risk is reduced.

Accelerate Fixes, Prevent Exposure
Delivers safe, context-aware fixes directly within IDEs, source control systems, and CLI, and applies the same reasoning pre-merge to prevent new exposure from entering production.
Prioritize Fixes That Matters
Determines which exposures are materially exploitable in your environment and prioritizes fixes that break attack chains across identity, network, and configuration.
Eliminate Backlog Noise
Eliminates non-exploitable findings through environmental reasoning, reducing manual triage load and focusing teams on defensible remediation decisions.
Remediation at a Different Speed.
Less noise. Faster fixes. Measurable exposure reduction.
Faster remediation of critical exposures
Reduction in false positives, reducing burnout and backlogs
Rise in remediation velocity — from 200+ days to minutes
What Sets Averlon Apart?
Most tools generate and aggregate findings. Averlon closes exposure.
Our AI agents don’t just rank risks, they generates safe fixes and deliver them straight into IDEs, GitHub, and CLI. Combined with autonomous exploitability and attack-chain analysis, Averlon closes the exposure window that leaves most organizations exposed.
Safe Fixes, Right Where Your Developers Work
AI agents deliver safe, context-aware fixes directly within IDEs, source control systems, and CLI. Remediation happens where work happens, no new systems. Every fix addresses potential breaking changes before delivery.

AI Agents That Triage and Prioritize
Autonomously determine what is materially exploitable in your environment and surface the exposures attackers are most likely to chain. Reduce decision load. Shrink your exposure window.

See Attack Chains Before Attackers Do
Attackers chain exposures across identity, network, and configuration. Averlon surfaces these chains so you can break them before they are exploited.



Exposures Impact Everyone. So Does Averlon.
Trusted by Security Leaders.
Hear from CISOs and security teams using Averlon to accelerate remediation and reduce risk
"Averlon has saved critical time in our 0-day incident response to issues such as the libWebp vulnerability (CVE-2023-4863). On a steady state basis, we expect it to save our security engineers hundreds of hours per month."


"Having used several leading vendors’ products, the visibility and insights Averlon provides is unmatched."


"Averlon enables customers to drastically reduce the effort and skill needed in discovering viable Attack Chains… significantly improves the effectiveness of remediations."


"Averlon cut through all the noise and brought attention to what vulnerabilities really matter… Attacks and Mitigations is a language that my board understands."


"Averlon cuts through the noise and gives my security teams visibility into the vulnerabilities that really matter. Its predictive attack intelligence allows for mitigations before real world attacks materialize."


"With the rise of AI, attacks are becoming more sophisticated. To stay ahead and successfully safeguard their organization, CISOs and their teams must learn how to think like attackers and anticipate how they breach cloud assets. Averlon solves this challenge, providing customers with a holistic way to understand, predict, and prevent cloud security attacks."


"Averlon is a powerful platform that allows enterprises to map exactly how an attacker can compromise an environment. By understanding the attacker’s view, Averlon gives CISOs and their teams unparalleled ability to prioritize what an attacker can explore or exploit to pinpoint threats, predict attacks, and to mitigate them."


Expert Insights to Fix Faster
Stay ahead with research and insights on exposures, remediation velocity, and security strategy.
Stop Drowning in Findings. Start Fixing.
Attackers move in days. Fixes take months.
Averlon closes that gap, helping you reduce material exposure before attackers exploit it.